Logging into Azure doesn’t have to be complicated. Whether you’re a developer, IT admin, or business owner, mastering the azure log in process is your first step toward unlocking cloud power securely and efficiently.
Azure Log In: Understanding the Basics

Before diving into advanced configurations, it’s essential to understand what the azure log in process actually entails. Microsoft Azure, as one of the leading cloud platforms, requires secure and authenticated access to manage resources, deploy applications, and monitor performance. The azure log in is the gateway to all these capabilities, serving as the foundational step in interacting with Azure services.
When you perform an azure log in, you’re not just accessing a dashboard—you’re authenticating your identity against Microsoft’s identity and access management system, Azure Active Directory (Azure AD). This ensures that only authorized users can access sensitive data and critical infrastructure. Azure supports multiple types of accounts, including personal Microsoft accounts, work or school accounts, and guest accounts, each with different access levels and use cases.
What Is Azure Active Directory?
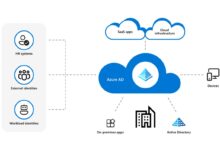
Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service. It plays a central role in the azure log in process by managing user identities, enforcing authentication policies, and enabling single sign-on (SSO) across thousands of cloud applications. Unlike traditional on-premises Active Directory, Azure AD is built for the cloud and integrates seamlessly with Office 365, Microsoft 365, and thousands of third-party SaaS apps.
Azure AD supports modern authentication protocols such as OAuth 2.0, OpenID Connect, and SAML 2.0, which are essential for secure logins across devices and platforms. When you initiate an azure log in, Azure AD verifies your credentials and issues security tokens that grant access to authorized resources. This token-based system enhances security by minimizing the exposure of passwords and enabling conditional access policies.
Different Types of Azure Accounts
There are several types of accounts you can use during the azure log in process. The most common include:
- Work or School Account: Assigned by an organization using Azure AD. These are typically in the format
user@company.comand are managed by IT administrators. - Microsoft Personal Account: Used for individual access to consumer services like Outlook.com, Xbox, or OneDrive. Can be used to sign in to Azure if granted access.
- Guest User Account: External users invited to collaborate within an Azure environment. Often used in B2B scenarios.
Understanding which account type you’re using is crucial because it determines your access rights, multi-factor authentication (MFA) requirements, and the administrative controls available to you during the azure log in experience.
“Azure AD is the backbone of identity in the Microsoft cloud. Every azure log in starts here.” — Microsoft Azure Documentation
Step-by-Step Guide to Azure Log In
Now that we’ve covered the foundational concepts, let’s walk through the actual process of performing an azure log in. This guide will help both new and experienced users navigate the login interface with confidence.
The standard azure log in process begins at portal.azure.com, the primary entry point for the Azure Management Portal. From there, users are prompted to enter their email address or phone number associated with their Microsoft account. After entering the identifier, the system determines whether it’s a personal, work, or guest account and routes the authentication accordingly.
Accessing the Azure Portal
To begin the azure log in, open your preferred web browser and navigate to https://portal.azure.com. This URL is the official and secure gateway to the Azure platform. Avoid using unofficial links or search engine ads, as they may lead to phishing sites.
Once on the page, you’ll see a clean login interface asking for your email, phone, or Skype username. After entering this information, click “Next.” The system will then check if the account exists in its directory and prompt for a password if valid. If the account is linked to multiple directories (e.g., multiple organizations), you may be asked to select the correct tenant before proceeding.
Entering Credentials and Authentication
After providing your username, the next step in the azure log in flow is entering your password. For added security, Azure often enforces strong password policies, including length, complexity, and expiration rules. If you’ve forgotten your password, Azure provides a “Forgot password?” link that guides you through a secure recovery process using registered contact methods.
Once the password is submitted, Azure evaluates the login request based on several factors, including location, device health, and sign-in risk. If multi-factor authentication (MFA) is enabled—which is highly recommended—the system will prompt you for a second verification method. This could include:
- A notification via the Microsoft Authenticator app
- A phone call or SMS code
- A hardware security key (e.g., YubiKey)
- Biometric verification on trusted devices
This layered approach ensures that even if a password is compromised, unauthorized access remains blocked.
Common Azure Log In Issues and How to Fix Them
Despite its robust infrastructure, users occasionally encounter problems during the azure log in process. These issues can stem from configuration errors, network problems, or security policies. Recognizing and resolving them quickly is vital for maintaining productivity.
One of the most frequent complaints is being unable to sign in due to incorrect credentials. However, in many cases, the issue isn’t a wrong password but rather an incorrect username format or a mismatched directory. For example, users might try logging in with user@gmail.com when their actual Azure account is user@company.onmicrosoft.com.
Forgot Password or Locked Account
If you’re unable to complete the azure log in due to a forgotten password, Azure offers a self-service password reset (SSPR) feature. This allows users to regain access without contacting IT support, provided they’ve registered recovery options such as a mobile number, alternate email, or security questions.
To use SSPR, go to the Azure password reset page and follow the prompts. You’ll need to verify your identity through at least one registered method. Once verified, you can set a new password and immediately use it to log in.
Similarly, accounts can become locked after multiple failed login attempts. This is a security measure to prevent brute-force attacks. In such cases, the account will automatically unlock after a cooldown period (usually 30 minutes), or an administrator can manually unlock it via the Azure portal.
Multi-Factor Authentication Failures
Multi-factor authentication (MFA) is a cornerstone of secure azure log in practices, but it can also be a source of frustration when it fails. Common causes include:
- The Microsoft Authenticator app not receiving push notifications
- Using an outdated phone number or email for verification
- Time synchronization issues on devices generating time-based one-time passwords (TOTP)
To resolve MFA issues, users should first ensure their contact information is up to date in their Azure profile. They can also register multiple verification methods as backups. Administrators can review sign-in logs in Azure AD to diagnose MFA-related failures and adjust policies if necessary.
“Over 99.9% of account compromises can be prevented by enabling MFA.” — Microsoft Security Report
Security Best Practices for Azure Log In
Securing the azure log in process is not just about convenience—it’s a critical component of your overall cloud security strategy. With cyberattacks on the rise, organizations must adopt proactive measures to protect their Azure environments from unauthorized access.
A key principle is the zero-trust model, which assumes that no user or device should be trusted by default, even if they’re inside the corporate network. This means every azure log in must be verified, encrypted, and monitored for anomalies. Implementing strong identity governance reduces the risk of data breaches and ensures compliance with regulations like GDPR, HIPAA, and SOC 2.
Enable Multi-Factor Authentication (MFA)
As previously mentioned, MFA is one of the most effective ways to secure the azure log in process. By requiring two or more forms of verification, MFA significantly reduces the likelihood of account takeover. Microsoft reports that enabling MFA blocks over 99.9% of automated attacks.
Organizations should enforce MFA for all users, especially administrators and those with access to sensitive data. Azure AD offers several MFA deployment options, including per-user activation and conditional access policies. Conditional access allows you to apply MFA rules based on specific conditions, such as user location, device compliance, or sign-in risk level.
Use Conditional Access Policies
Conditional Access is a powerful feature in Azure AD that enables organizations to automate access control decisions based on real-time signals. For example, you can create a policy that requires MFA when a user logs in from an unfamiliar location or blocks access from unmanaged devices.
To set up Conditional Access, navigate to the Azure portal, go to Azure Active Directory > Security > Conditional Access, and create a new policy. You can define conditions such as:
- User or group membership
- Cloud app or workload
- Device platform (iOS, Android, Windows)
- Sign-in risk detected by Azure AD Identity Protection
These policies ensure that the azure log in process adapts dynamically to potential threats, providing a balance between security and usability.
Using Azure CLI and PowerShell for Log In
While the web portal is the most common way to perform an azure log in, many developers and system administrators prefer command-line tools like Azure CLI and Azure PowerShell for automation and scripting. These tools offer powerful alternatives to GUI-based access and are essential for DevOps workflows.
The Azure Command-Line Interface (CLI) is a cross-platform tool that allows you to manage Azure resources through scripts and terminal commands. To start using it, you must first authenticate via the azure log in command. Similarly, Azure PowerShell provides cmdlets for managing Azure services using PowerShell scripts, requiring authentication before execution.
Logging In with Azure CLI
To log in using Azure CLI, open your terminal or command prompt and run the following command:
az loginThis command opens a browser window where you can complete the standard azure log in process. Once authenticated, the CLI stores an access token that allows you to run commands without re-authenticating for a limited time.
For non-interactive scenarios (e.g., CI/CD pipelines), you can use service principals or managed identities instead of interactive login. A service principal is a security identity used by applications, services, and automation tools to access Azure resources. You can create one using the Azure portal or CLI and assign it specific roles via Role-Based Access Control (RBAC).
Authenticating with Azure PowerShell
Azure PowerShell uses the Connect-AzAccount cmdlet to initiate the azure log in process. Run the following command in a PowerShell session:
Connect-AzAccountLike the CLI, this opens a browser window for authentication. After successful login, you can manage subscriptions, deploy templates, and query resources using PowerShell scripts.
For automated environments, consider using managed identities, which allow Azure resources (like VMs or App Services) to automatically obtain credentials from Azure AD without storing secrets in code. This eliminates the need for hardcoded credentials and enhances security.
Azure Log In for Organizations: Managing User Access
In enterprise environments, the azure log in process is not just about individual access—it’s about governance, compliance, and scalability. IT administrators must ensure that users have the right level of access, that credentials are managed securely, and that audit trails are maintained.
Azure AD provides robust tools for managing user identities at scale. From creating users and assigning licenses to enforcing password policies and monitoring sign-ins, administrators have granular control over the entire identity lifecycle. This is especially important in hybrid environments where on-premises directories are synchronized with Azure AD using tools like Azure AD Connect.
User and Group Management
Effective user management begins with organizing identities into logical groups. In Azure AD, you can create security groups and Microsoft 365 groups to simplify access control. For example, instead of assigning permissions to individual users, you can assign a role to a group, and any new member automatically inherits the appropriate access.
When a new employee joins the organization, administrators can create a user account in Azure AD and assign them to relevant groups. This triggers automatic access to assigned applications and resources upon their first azure log in. Similarly, when an employee leaves, disabling or deleting their account immediately revokes access across all integrated services.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a fundamental security model in Azure that limits user access to only what they need. RBAC uses built-in roles like Owner, Contributor, and Reader, as well as custom roles, to define precise permissions.
For example, a developer might have Contributor access to a specific resource group, allowing them to deploy and manage resources but not delete the entire group. An auditor might have Reader access to view configurations without making changes. Properly configuring RBAC minimizes the risk of accidental deletions or malicious actions during the azure log in session.
“Least privilege access is not just a best practice—it’s a necessity in cloud security.” — NIST Guidelines
Advanced Azure Log In Methods: SSO and Federation
For large organizations and service providers, basic username-and-password authentication isn’t always sufficient. Advanced azure log in methods like Single Sign-On (SSO) and federation enable seamless, secure access across multiple applications and domains.
Single Sign-On allows users to log in once and gain access to multiple systems without re-entering credentials. In Azure, SSO is often implemented using SAML, OAuth, or OpenID Connect. This is particularly useful in environments where users interact with dozens of cloud apps daily.
Configuring Single Sign-On (SSO)
To set up SSO in Azure, administrators can integrate third-party applications through the Azure AD App Gallery or configure custom apps manually. The process typically involves:
- Uploading a SAML metadata file or entering configuration URLs
- Mapping user attributes between Azure AD and the application
- Assigning users or groups to the application
Once configured, users can access the application directly from the My Apps portal (https://myapps.microsoft.com) after completing a single azure log in. This reduces password fatigue and improves user experience.
Federated Identity with On-Premises AD
Many enterprises use federated identity to extend their on-premises Active Directory to the cloud. This setup allows users to log in to Azure using their corporate credentials without storing passwords in the cloud.
Tools like Active Directory Federation Services (AD FS) or third-party identity providers (IdPs) can be used to establish trust between on-premises systems and Azure AD. When a user attempts an azure log in, authentication is redirected to the on-premises IdP, which validates the credentials and sends a security token back to Azure AD.
This method enhances security by keeping password hashes on-premises and enables seamless integration with existing identity infrastructure.
How do I reset my Azure password?
You can reset your Azure password by visiting the self-service password reset page at https://aka.ms/sspr. Follow the prompts to verify your identity using a registered phone number, email, or security question, then set a new password.
Why can’t I log in to Azure even with the correct password?
This could be due to several reasons: incorrect username format, being in the wrong Azure AD tenant, multi-factor authentication failure, or account lockout. Check your sign-in logs in Azure AD for detailed error messages.
What is the difference between Azure AD and on-premises AD?
Azure AD is a cloud-native identity service designed for modern authentication and SaaS app access, while on-premises AD is a directory service for Windows networks. Azure AD supports REST APIs, OAuth, and SAML, whereas on-premises AD relies on LDAP and Kerberos.
Can I use Azure CLI without interactive login?
Yes, you can use service principals or managed identities to authenticate Azure CLI in non-interactive environments like scripts or CI/CD pipelines. This avoids the need for manual azure log in and improves security by eliminating password storage.
How do I enable MFA for my Azure account?
Go to the Azure portal, navigate to Azure Active Directory > Users > Multi-Factor Authentication, and enable it for individual users or use Conditional Access policies to enforce it organization-wide.
Mastering the azure log in process is essential for anyone working with Microsoft’s cloud platform. From basic portal access to advanced federation and automation, understanding the nuances of authentication ensures secure, efficient, and scalable operations. By following best practices like enabling MFA, using Conditional Access, and leveraging command-line tools, you can optimize both security and productivity in your Azure environment.
Recommended for you 👇
Further Reading: